Understanding Zero Trust Architecture
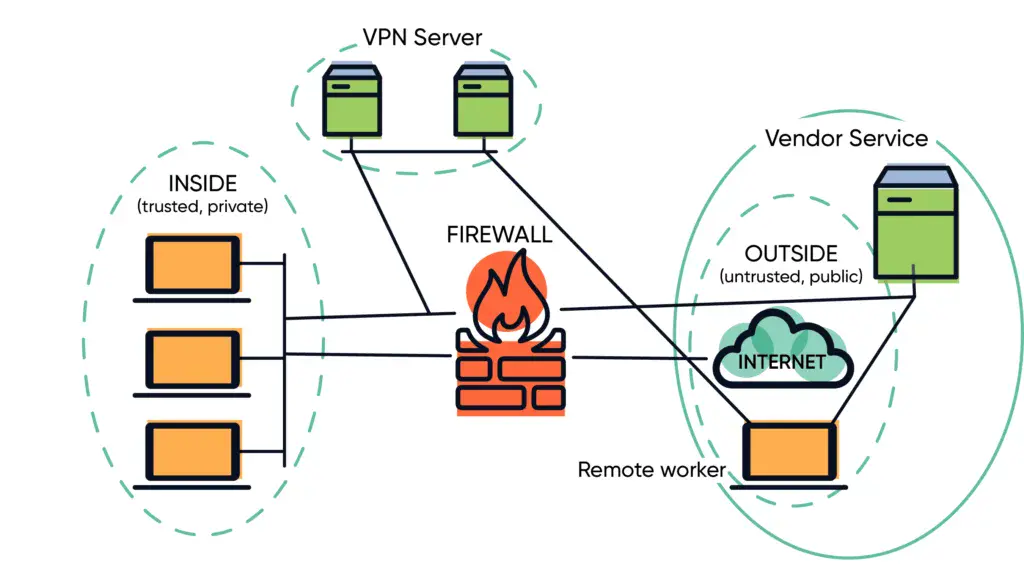
Zero Trust Architecture (ZTA) is a security framework that operates under the principle of "never trust, always verify." This approach assumes that threats could be both external and internal, and thus, no user or device should be trusted by default, regardless of their location within the network perimeter. By implementing ZTA, organizations can enhance their security posture and mitigate risks associated with data breaches and cyber threats.
Core Principles of Zero Trust Architecture
The following are the fundamental principles that guide the implementation of Zero Trust Architecture:
- Least Privilege Access: Users and devices are granted the minimum level of access necessary to perform their tasks. This principle ensures that users can only access resources essential for their work, reducing the risk of unauthorized access.
- Micro-Segmentation: Networks are divided into smaller, manageable segments. This limits the lateral movement of attackers within the network, making it more difficult for them to access sensitive data.
- Continuous Monitoring: Continuous monitoring of user activity and network traffic is critical. By analyzing patterns and behaviors, organizations can detect anomalies that may indicate a security breach.
- Multi-Factor Authentication (MFA): Implementing MFA enhances security by requiring users to provide multiple forms of verification before accessing resources. This adds an extra layer of protection against unauthorized access.
- Data Encryption: Encrypting data both at rest and in transit ensures that sensitive information remains protected, even if it is intercepted by malicious actors.
Implementing Zero Trust Architecture
Transitioning to a Zero Trust Architecture involves a strategic approach that includes several steps:
1. Assessing Current Security Posture
Before implementing ZTA, organizations must conduct a thorough assessment of their current security posture. This includes identifying existing vulnerabilities, mapping out the network, and understanding the data flow within the organization.
2. Defining Protect Surface
Unlike traditional security models that focus on protecting the network perimeter, Zero Trust emphasizes protecting valuable data and assets. Organizations should identify their protect surface, which includes sensitive data, applications, and systems that need to be secured.
3. Implementing Identity and Access Management (IAM)
Effective Identity and Access Management is crucial in a Zero Trust model. Organizations must deploy robust IAM solutions to manage user identities, roles, and access rights, ensuring that only authorized individuals can access specific resources.
4. Enforcing Policies and Controls
Once IAM is in place, organizations should establish policies and controls that dictate how users can access resources. These policies should be regularly reviewed and updated to adapt to evolving threats.
5. Utilizing Security Technologies
To support the Zero Trust Architecture, organizations should leverage various security technologies, including:
- Next-Generation Firewalls (NGFW): NGFWs provide advanced threat detection and prevention capabilities, allowing organizations to monitor and control network traffic effectively.
- Endpoint Detection and Response (EDR): EDR solutions help organizations detect and respond to threats on endpoints, providing visibility into user and device behavior.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security data in real-time, helping organizations identify and respond to threats quickly.
The Benefits of Zero Trust Architecture
Adopting Zero Trust Architecture offers numerous benefits for organizations, including:
- Enhanced Security: By validating every access request and enforcing strict access controls, ZTA significantly reduces the risk of data breaches and insider threats.
- Improved Compliance: ZTA helps organizations meet regulatory compliance requirements by ensuring that sensitive data is adequately protected and monitored.
- Increased Visibility: Continuous monitoring and detailed logging provide organizations with better visibility into their network, enabling them to detect and respond to threats more effectively.
- Adaptability: ZTA allows organizations to quickly adapt to changing security landscapes and emerging threats, ensuring that their defenses remain robust over time.
Challenges in Implementing Zero Trust Architecture
While the benefits of Zero Trust Architecture are substantial, organizations may face several challenges during implementation:
- Complexity: Transitioning from a traditional security model to ZTA can be complex and may require significant changes to existing infrastructure and processes.
- Cost: Implementing ZTA can incur higher upfront costs, including investments in new technologies and training for IT staff.
- Cultural Resistance: Employees may resist changes to access policies and security protocols, particularly if they perceive them as burdensome.
Conclusion
Zero Trust Architecture represents a significant shift in how organizations approach security. By adopting its principles, organizations can create a more resilient and secure environment that protects against evolving cyber threats. Although there are challenges in implementation, the long-term benefits of enhanced security and compliance make ZTA a worthwhile investment. As cyber threats continue to grow in sophistication, the Zero Trust model will play a crucial role in safeguarding sensitive data and maintaining trust in digital transactions.






